
T1.accessPredictor
check for any memory access violations before
even flashing the software

check for any memory access violations before
even flashing the software
Upset by MPU exceptions in the field? Tracking them down while the software executes can be very time consuming and costly. T1.accessPredictor allows you to check for any memory access violations before even flashing the software. Think of it as an “off-line MPU”.

Analyzing the binary rather than the source code has significant advantages.

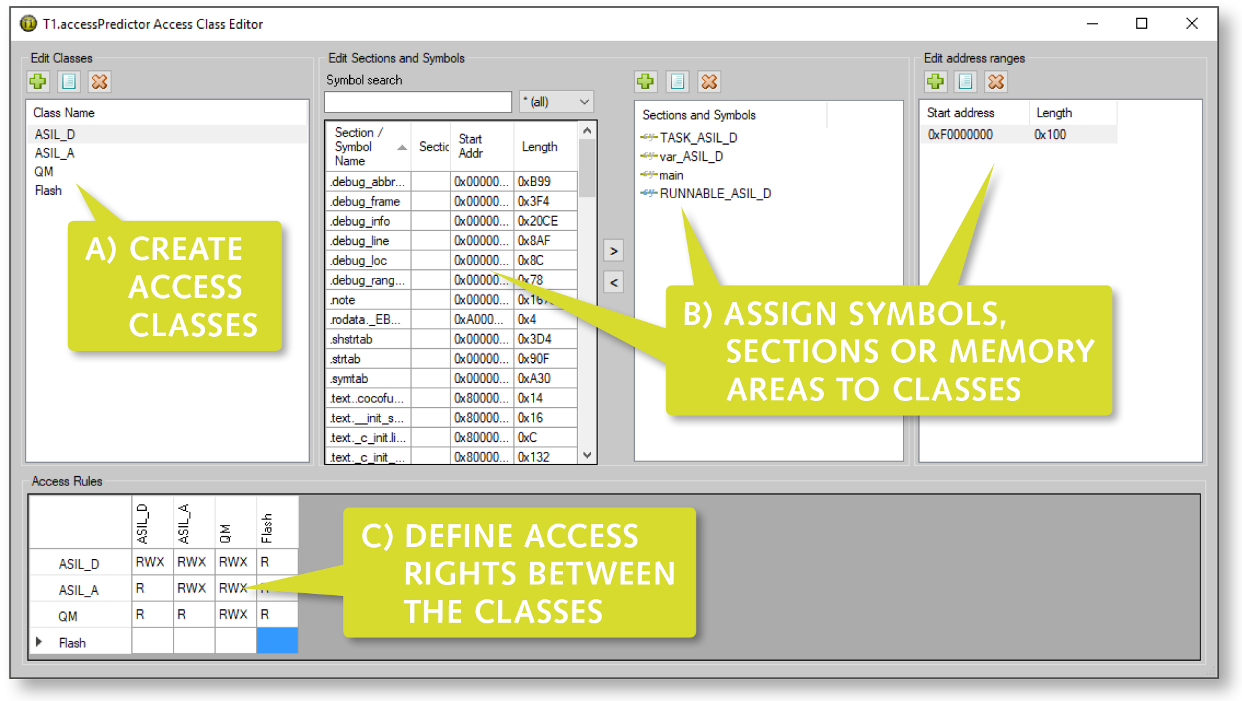
Specify the different access classes using the intuitive GUI and define in which way (Read, Write and eXecute) every class may access the other classes. “Execute” refers to code accesses such as function-calls. In the example below, four access-classes were defined: ASIL_A, ASIL_D, QM and Flash.
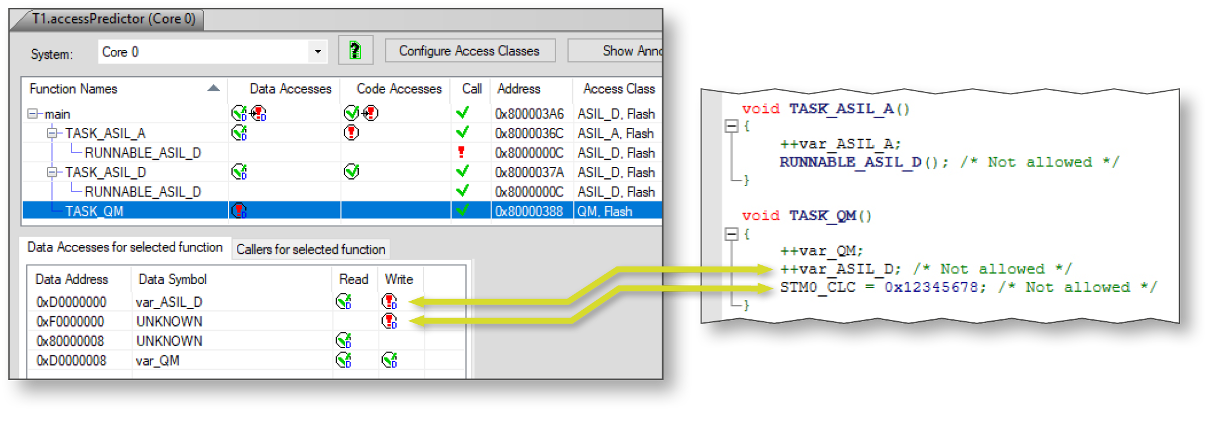
Read in the binary, the ELF file. T1.accessPredictor will disassemble the binary and perform a static analysis based on abstract interpretation. Afterwards T1.accessPredictor presents a “bi-directional” call-tree indicating a) which function calls which other functions and b) by which other functions a function gets called.
If necessary, add annotations (manually, generated or measurement-based) to complete the call-tree.
Analyze the results! The call-tree indicates access violations with red exclamation marks: for invalid data accesses and for invalid code accesses.
Export the results for regression tests for subsequent software releases.
| Silicon/IP Vendor |
Core | Controller Examples |
|---|---|---|
| Infineon | TC1.6.X, TC1.8 | TC2xx, TC3xx, TC4x |
| NXP/STM | e200z0-z4, z6, z7 | MPC57xx, MPC56xx, MPC55xx, SPC58xx, SPC57xx, SPC56xx, etc. |